Depending on the setup, there are various ways to configure a MikroTik’s WiFi for guest access. In this example, I’ll be using the MikroTik RB951G-2Hnd router, which has built-in WiFi. I’ll be using MikroTik’s Virtual AP feature to create a second SSID for guest access. Guests connecting to this SSID will have internet access, but more importantly, guests on the WiFi network will be connected to a separate subnet than those who are connected to the private WiFi. To further elaborate, the environment in this example already has WiFi setup for private use. The private WiFi is on the same subnet (192.168.100.0/24) as the private network. In addition, we’ll set up internet access for guests via WiFi on a different subnet (10.10.10.0/24), while blocking access to devices on the private network.
Step 01: Create a Virtual AP
Creating a Virtual AP will essentially create the new SSID for the guest network, which will later be assigned to 10.10.10.0/24. The Virtual AP is a network interface that will require the configuration of a Seucrity Profile, Virtual AP name, and Wireless settings (SSID, Master Interface, Security Profile assignment).
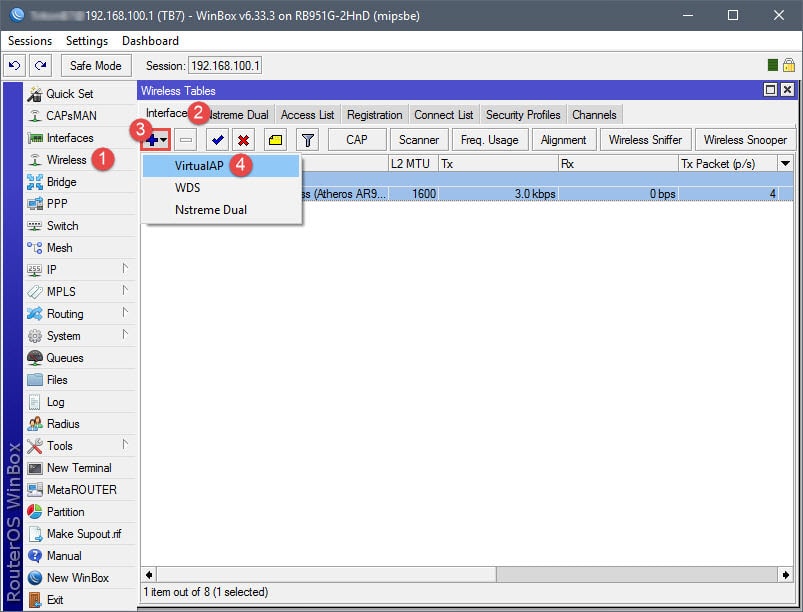
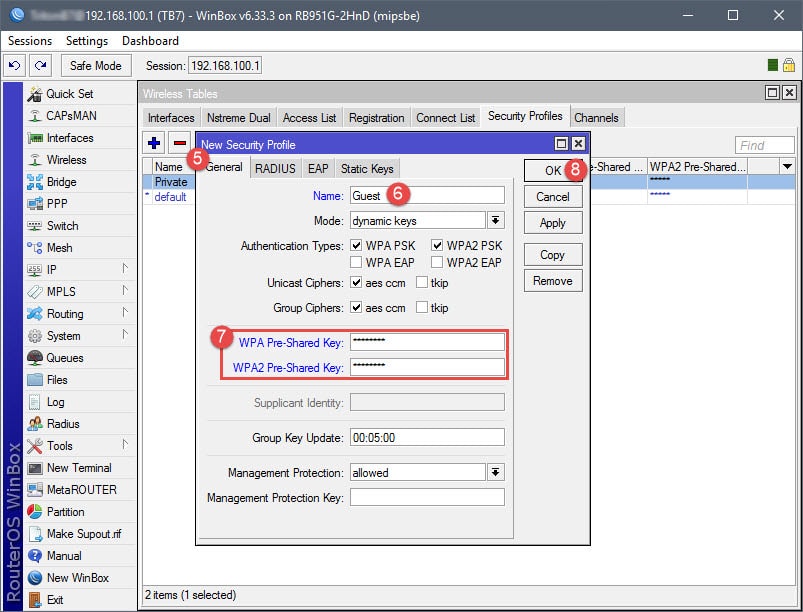
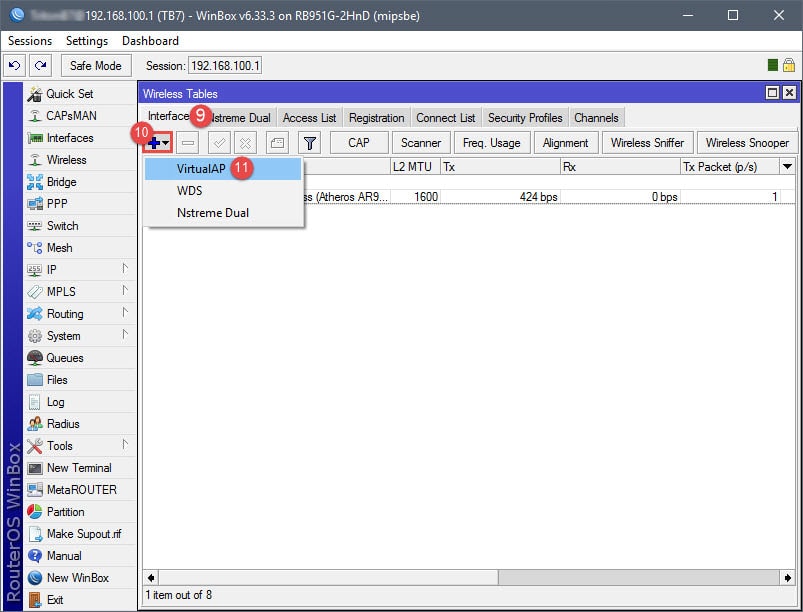
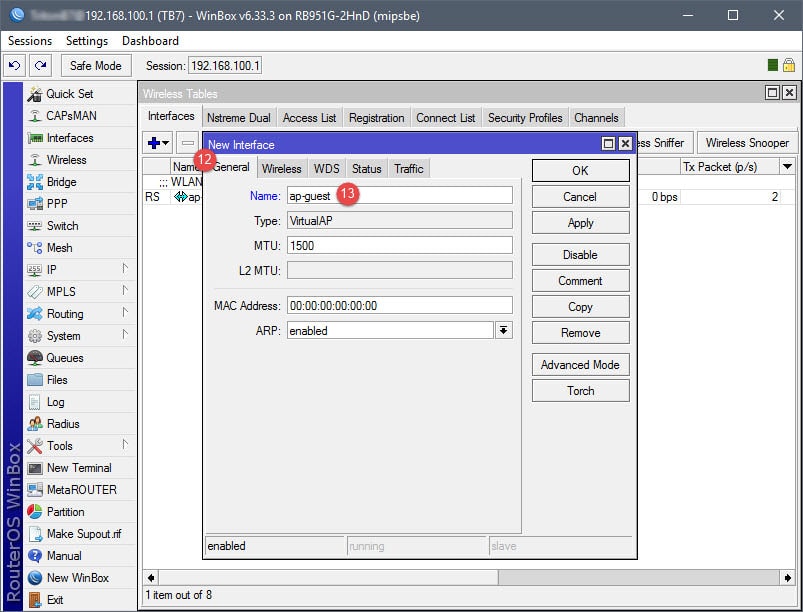
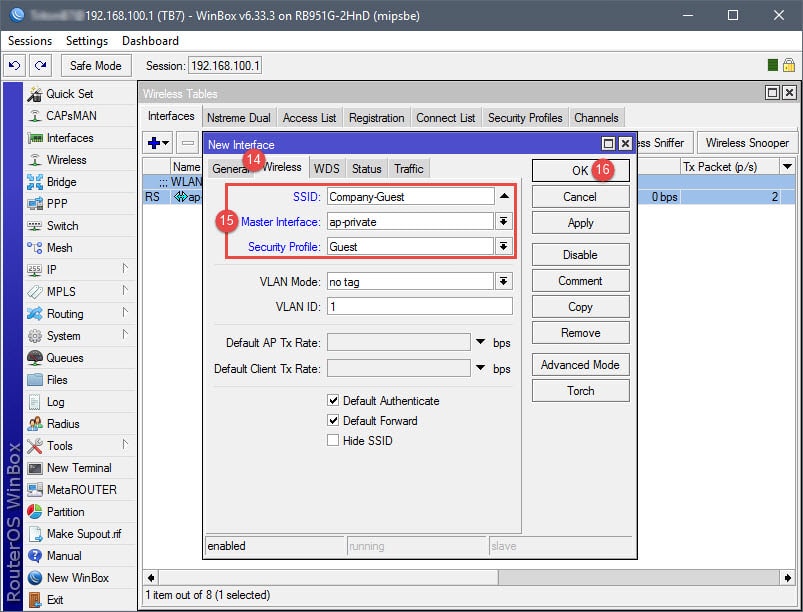
Step 02: Assign IP to Virtual AP
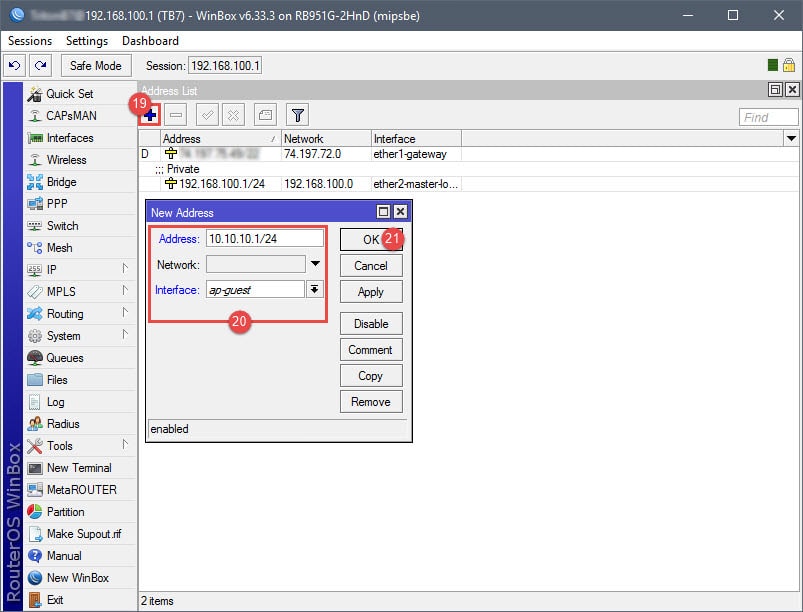
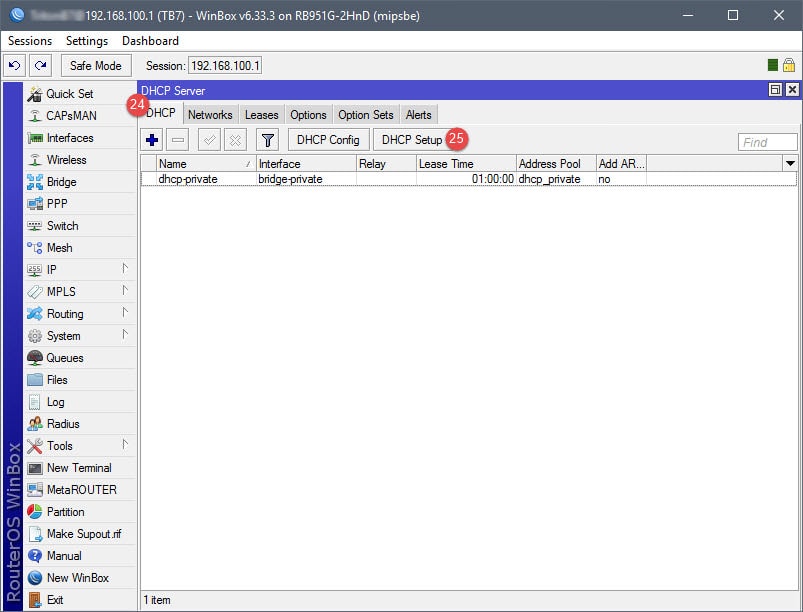
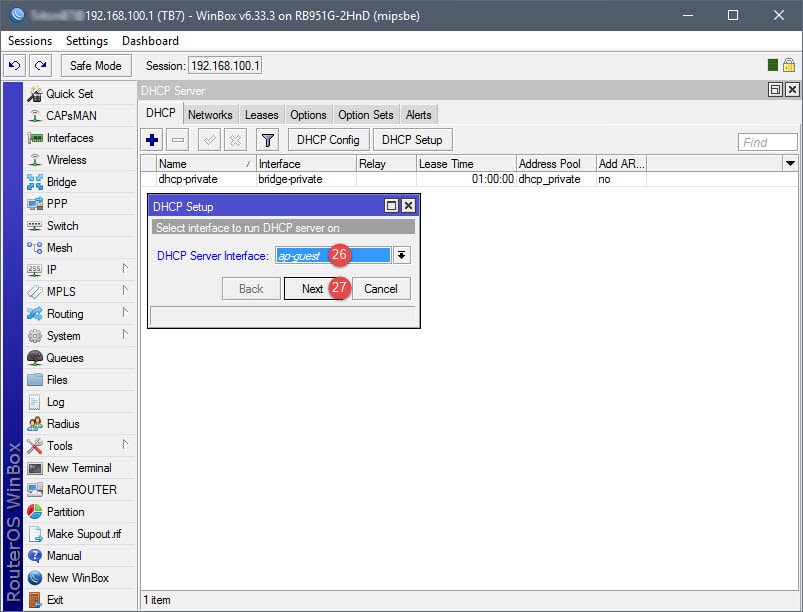
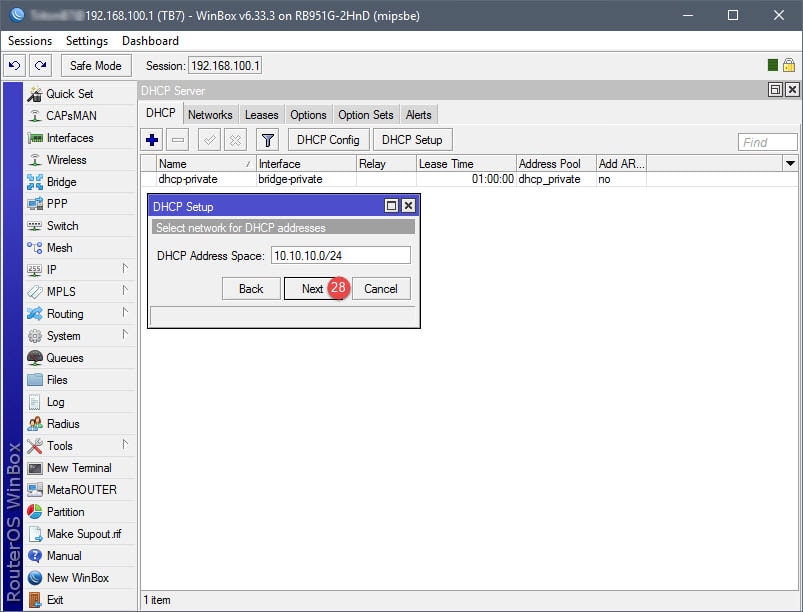
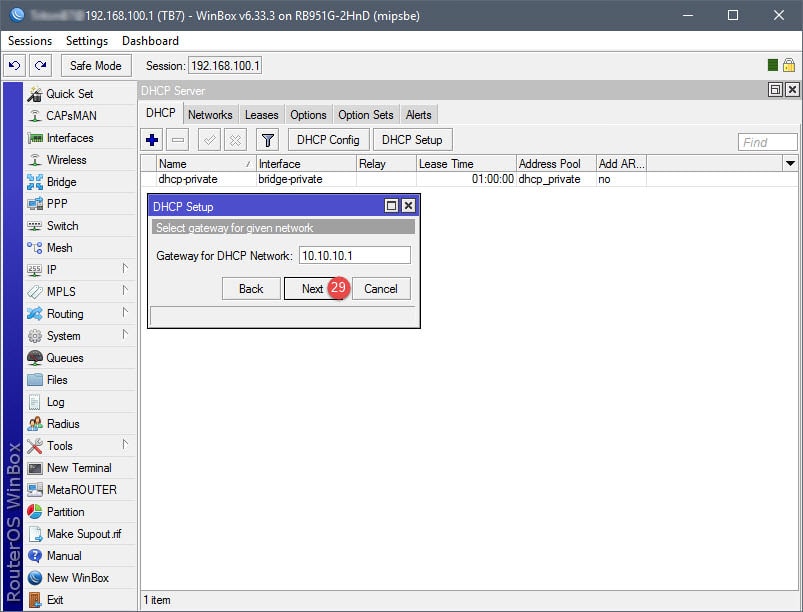
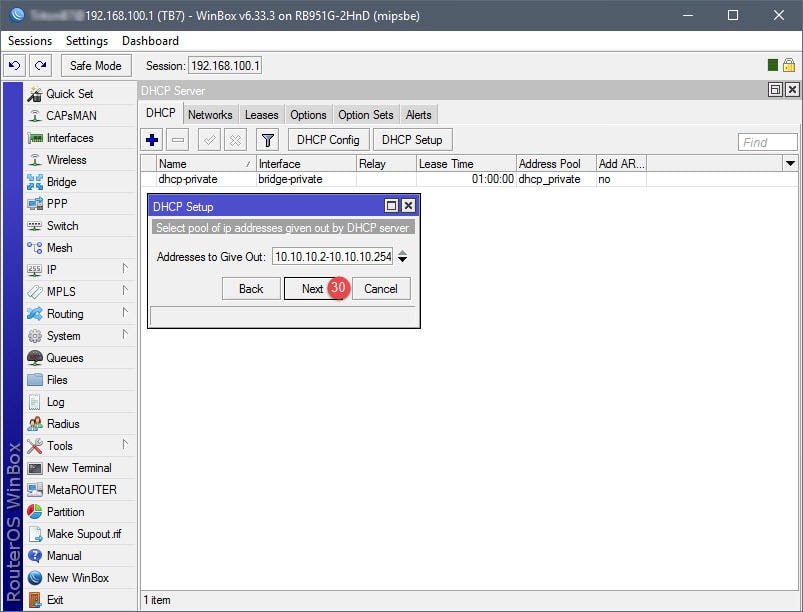
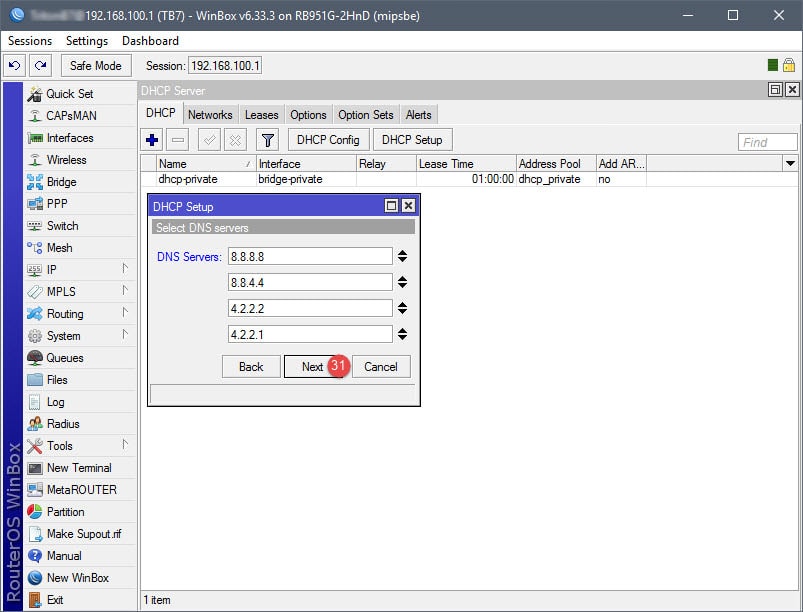
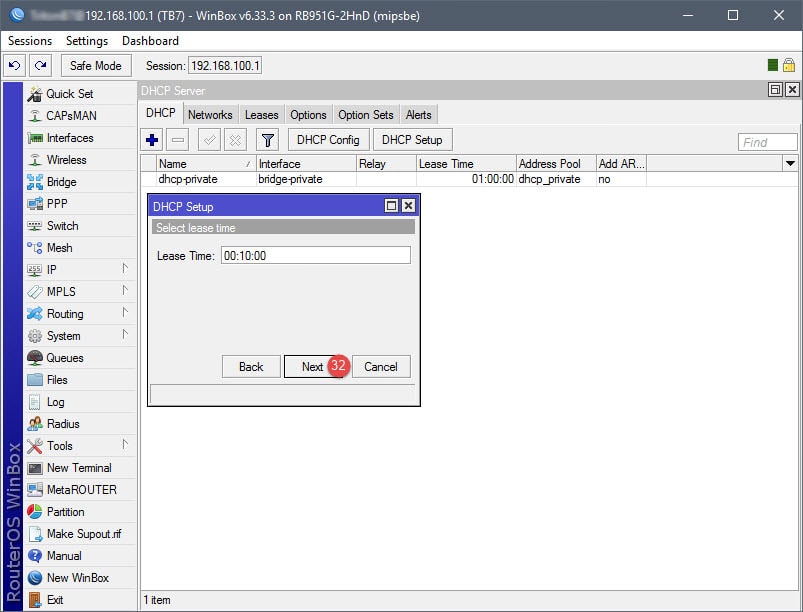
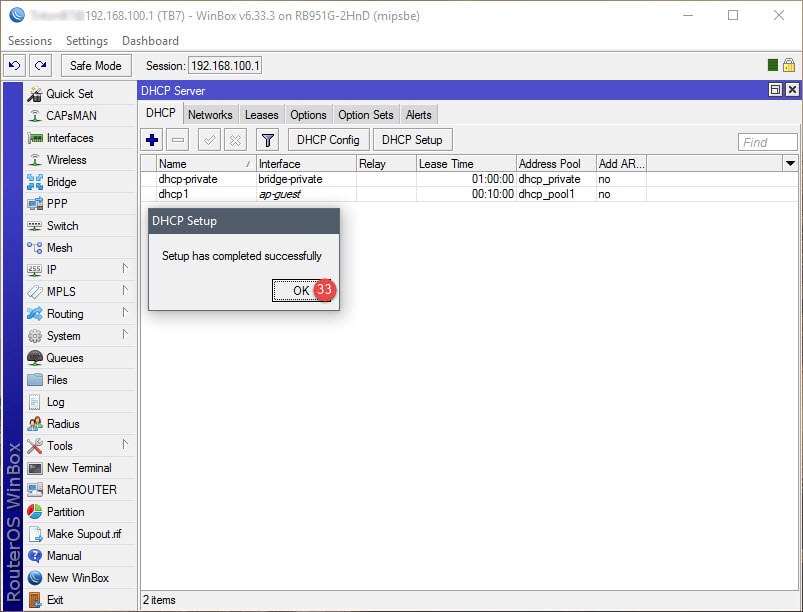
Step 03: Setup DHCP for Guest Network
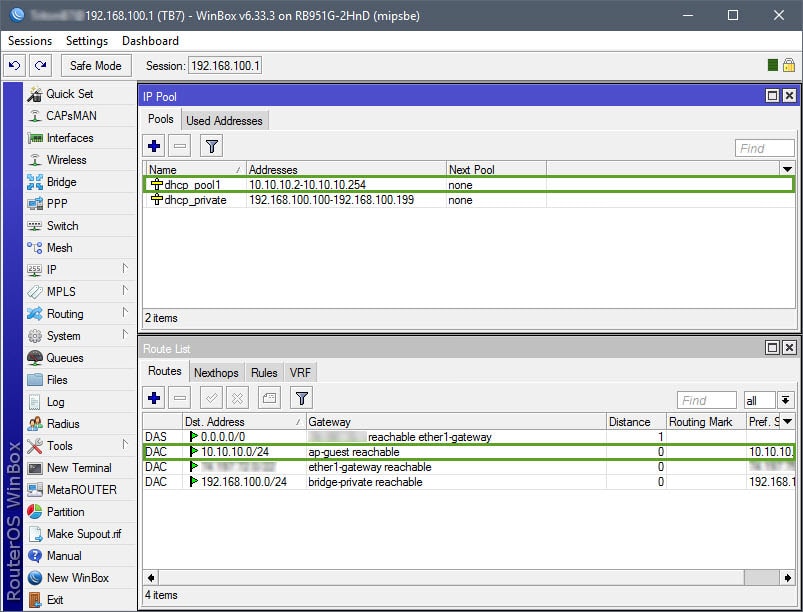
The DHCP setup is straightforward. A DHCP server will need to be assigned to the ap-guest interface, along with an IP scope, IP address space, gateway, IP address pool (IP addresses to give out for guests), DNS servers, and lease time. Note that the IP address pool in this example begins with 10.10.10.2, that’s because 10.10.10.1 has already been assigned to the Virtual AP interface.
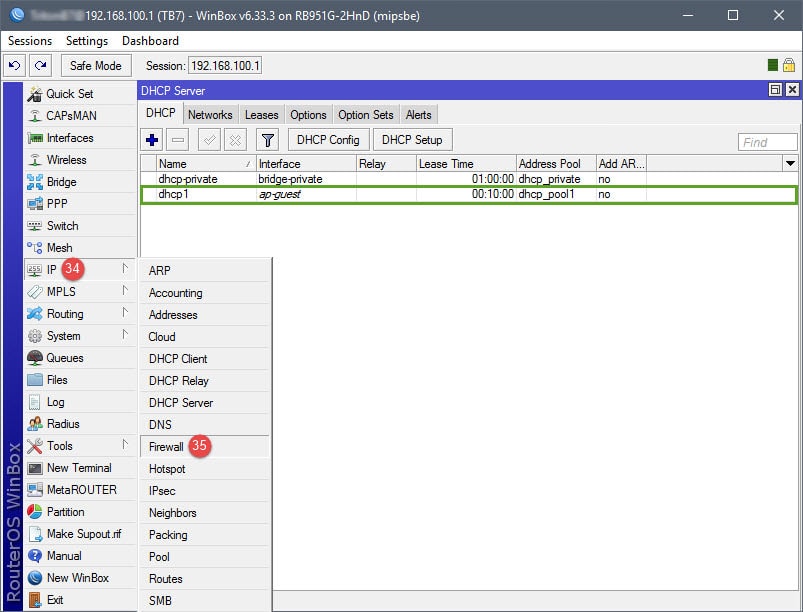
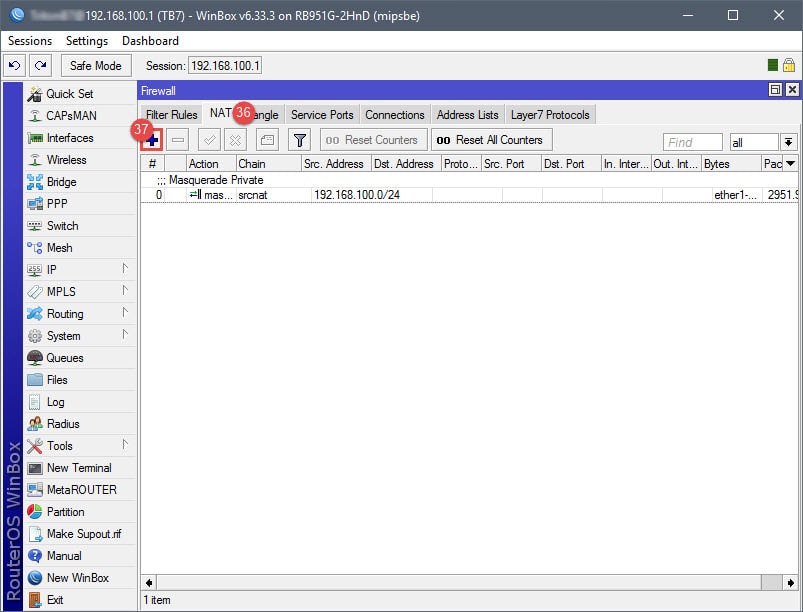
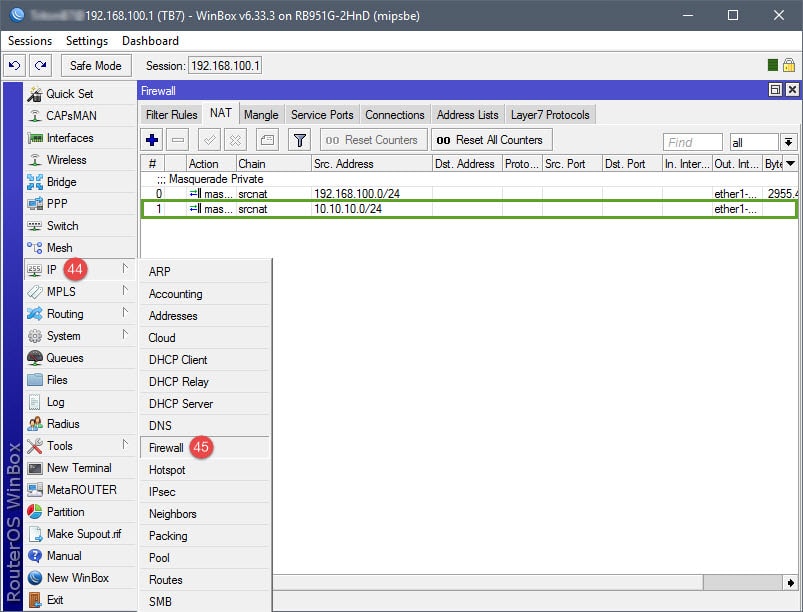
Step 04: Setup NAT Rules
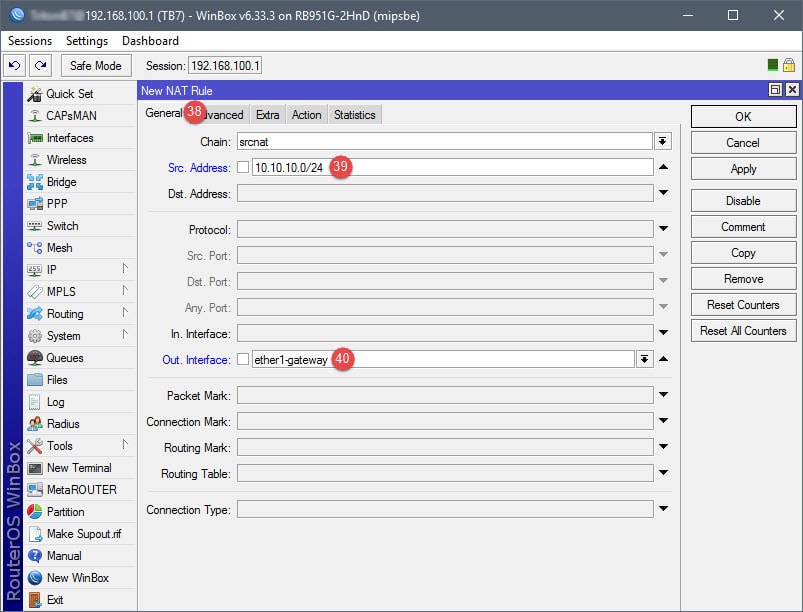
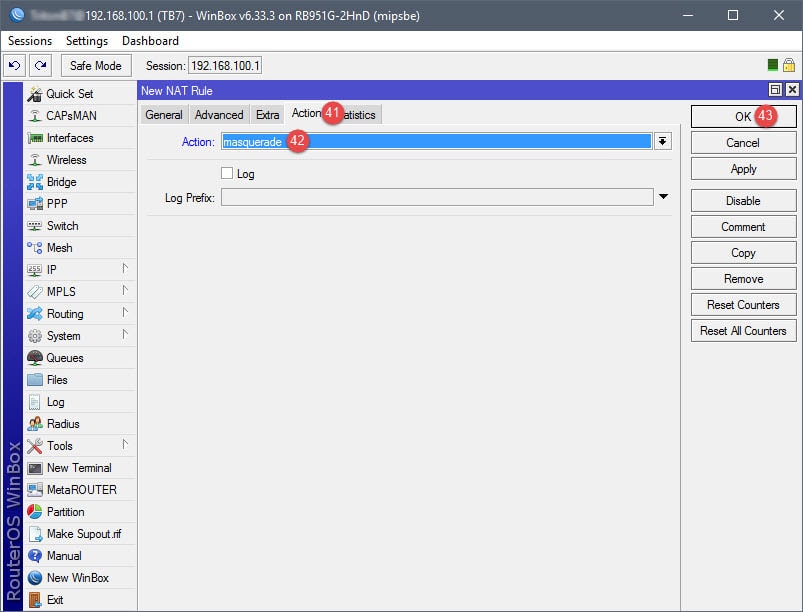
The NAT rule will be your basic masquerade rule to allow connected guests internet access. In this example, I simply used the subnet for the guest network (10.10.10.0/24). However, if you’d like, you can use an Address List to represent the subnet.
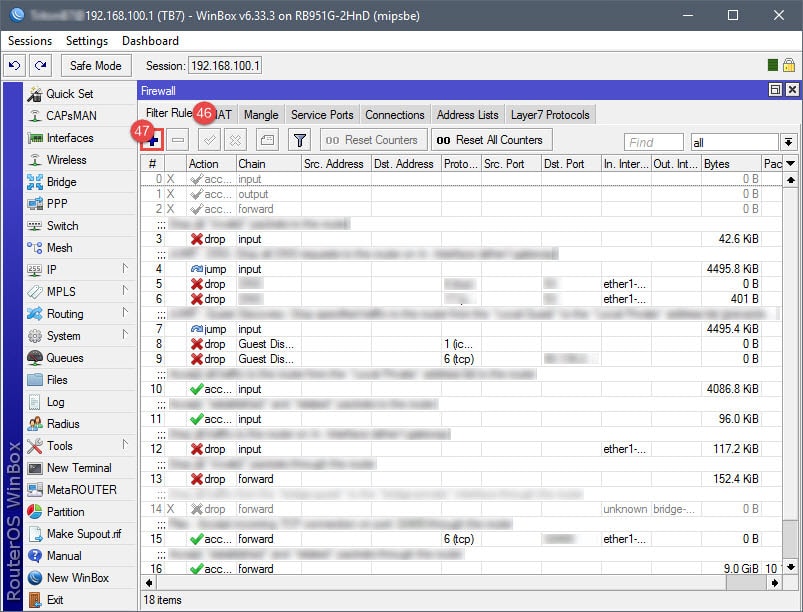
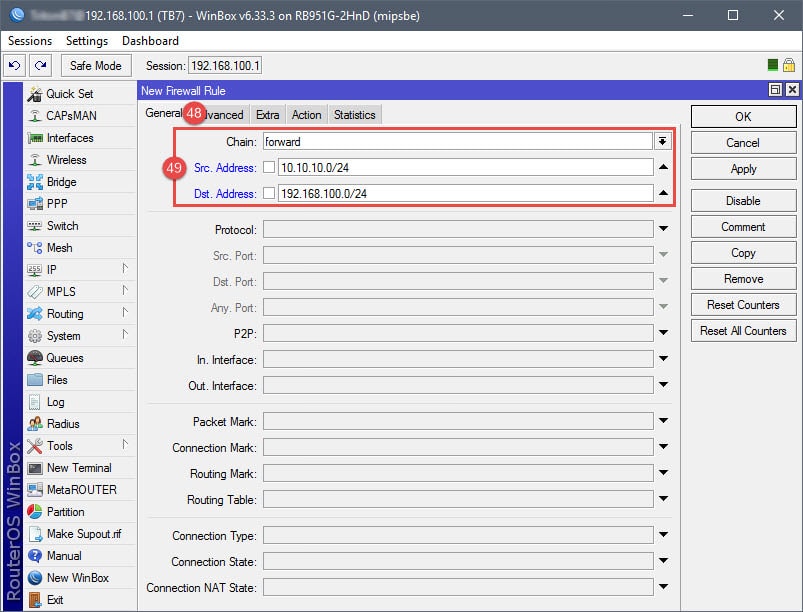
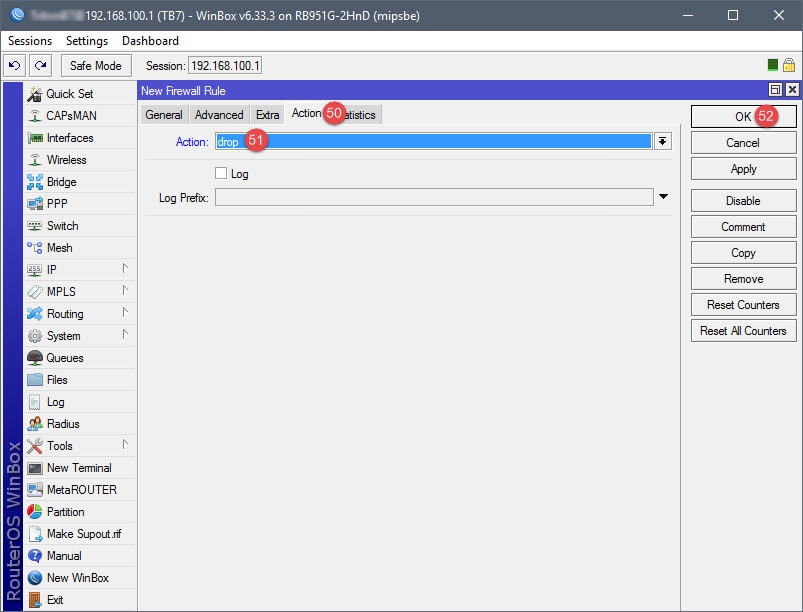
Step 05: Setup Firewall Rules
This firewall rule will only block the guest network from accessing the private network – this is a personal preference. If you’d like, a second rule can be added to block the private network from accessing the guest network. In addition, should you decide to establish bandwidth caps (Queues) for the guest network, ensure that the firewall isn’t using FastPath/FastTrack to route network traffic for the guest network. Queues will ignore all network traffic from devices that are hitting the FastPath/FastTrack firewall/filter rules.

Hi! Great tutorial!
I am trying to create a guest WiFi network on my Mikrotik router which is 10.10.10.0/24. The goal is to restrict the guests to access my home network which is 192.168.1.0/24. Following this guide everything works OK except one think. Guest cant access my WEB/MAIL/VOIP etc. servers, connected on the home network. Of course they are trying to reach them via Internet not via internal IP address. I thought that masquerade is going to deal with this, but obviously I’m missing something. I cant understand how the router still recognizes guests as guests when they once exit to the Internet?
Thanks!
Regards Stanko.
Stanko Topalov,
Masquerade will allow your guests internet access. Once on the internet if you have your WEB/MAIL/VOIP open to the public then your guest network will be able to access these services as well once guest traffic leaves your routers WAN port and comes back through your routers WAN port to access your WEB/MAIL/VOIP. You can add forward rules in your firewall to block guests from accessing these services internally on your local network though.
One idea, but not tested, is that if you dont want guests to access your WEB/MAIL/VOIP services on your local network and depending if your using static ip or DDNS to connect to the router/services, you could block forward traffic coming from WAN to WEB/MAIL/VOIP with your IP over the specific port being used by those services, or block your DDNS address (redirect to 127.0.0.1 etc) for guests, which would be easier and most likely more reliable.
In newer versions of router OS (6.43) you can not asign DHCP to virtual port.
I created new bridge (BridgeGuest for example), adigned virtual WiFi port to BridgeGuest , and asigned DHCP to BridgeGuest.
Also I asigned IP to BridgeGuest not to virtual WiFi port
Hello Boris,
Thank you for pointing this out. I recently tried this again and the bridge method you used is what I’ll be creating a new guide for.
Have you made this guide?
There is a new guide here: https://www.marthur.com/networking/mikrotik-setup-guest-vlan-wifi/2582/
MARTHUR, thanks a lot! I’ve been trying to set up Mikrotik cAP lite RBcAPL-2nd with guest wifi for couple days and only your article helped me. Built in WISP AP, Home ap didn’t work. Thanks a bunch.
Much appreciated on the tutorial. I have a Mikrotik Hex without the wireless AP, but just created a VLAN instead of Virtual AP and created a SSID in my TPLink AP assigned to the same VLAN ID. Worked like a champ!
Everything works Perfect. Thanks for the great tutorial.